
My data was held ransom. And I did it on purpose.
Other · Aug 9, 2016
I receive spam in my personal email almost daily. Usually I just ignore it and delete right away. However, I’ve gotten a bit more curious since I’ve become more immersed in security. What would happen if I actually clicked?
Social Engineering: to click or not to click
With one or two wrong clicks, your computer can become infected with a virus or Trojan. You may not even notice, and someone may have complete control of your computer – watching you through your webcam, browsing your files, stealing your passwords and recording all of your keystrokes.
It is far too easy for cyber criminals to lure you into clicking. They will try every social engineering trick in the book. These tricks include email subject lines like "Notice to appear in court" or "Unpaid Invoice" or "Order Form" and the list goes on.
I too even sometimes pause and have to think twice before clicking. And I’m a security expert. What about regular computer users who don’t have the same experience and level of education that I have? So I decided to click, with the goal of showing you what actually happens when you fall prey to ransomware.
The stages of a typical ransomware attack
I received an email from “FedEx” and decided to click. Before clicking though, I moved the content of the email into an isolated virtual machine. Subject line: "We could not deliver your parcel."
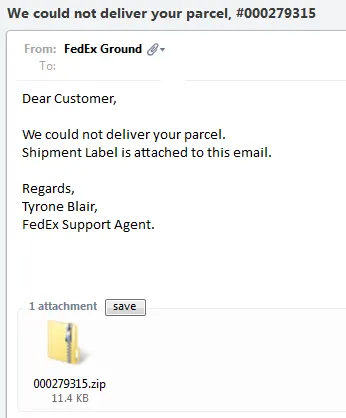
First Indicator - Email Address
Is the email really from FedEx? Of course not. Just look at the email address. In the majority of cases, the email address is a hacked email address of another victim or it’s setup by cyber criminals exclusively for the threat campaign.
Second Indicator - Attachment or Link
If the attacker has setup a phishing page and wants you to visit it, there will be a link in the email. Of course, everyone will advise not to click on a link or attachment from an unknown source. But that doesn’t always account for social engineering. People will make mistakes. In this case, the attachment was a zip file, and it contained one file: 000279315.doc.js.
Third Indicator - Double Extension
This file has double extension – .doc.js. By default, a Windows computer will hide the known extension, so the file may appear as 000279315.doc. Recently, JavaScript is being used actively for downloading Trojans or malware.
Game Over
Once I clicked on the file, this ransom note appeared on the screen:

As I mentioned, I was doing the experiment on a test virtual machine that had existing sample picture files. When I checked, those files were indeed encrypted. The links to download the decryption solution were active but required payment to proceed:
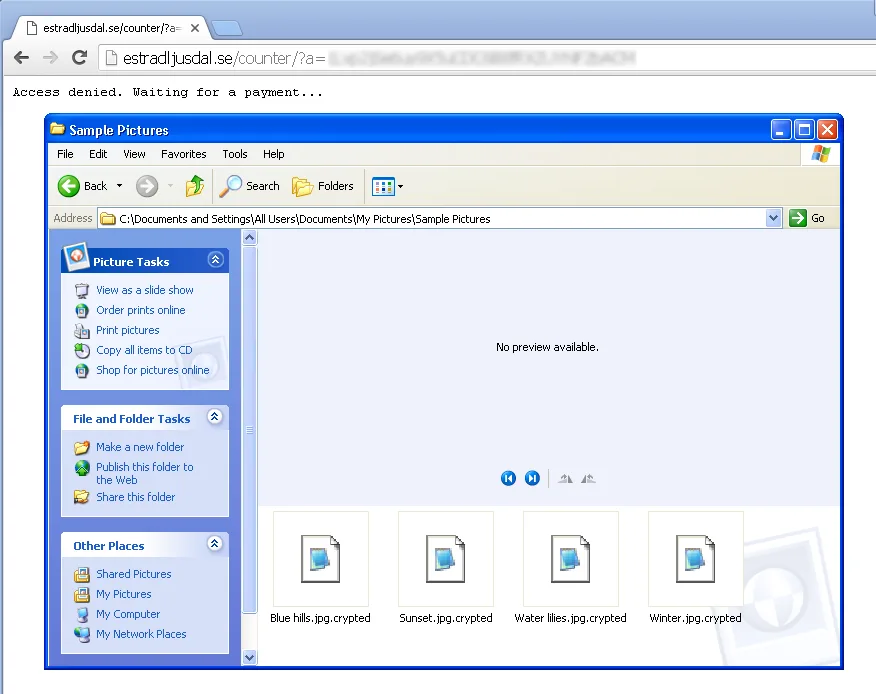
If this was a real computer with real data – think years of family photos or business documents with no offline backup – I would have no choice but to pay 0.50815 bitcoin (equivalent of 443.68 Canadian dollars) to get my files back.
Precautions you can take
Ransomware is not going away anytime soon. In fact, attacks are only growing in frequency and pervasiveness. It’s a pretty profitable business for cyber criminals. Every other week, we hear about a new ransomware variant being detected. I strongly recommend the following precautions:
- Back up regularly offline: if your backup drive is connected to your computer, most ransomware will encrypt files on it as well
- Think before you click: do not click on links or attachments from unknown sources. Verify that the email address is valid
- Invest in the right technology: use an anti-virus solution and keep it up to date
- Update religiously: take the time to download regular operating system updates to stay current
For advanced computer users, I would also recommend:
- Disable "Hide extensions for known file types" so you can see the actual extension of the file
- Enable "Show hidden files, folders, and drives" so you can see all files and folders
- When you receive a spam email with a malicious attachment (1) share the sample by uploading it onVirusTotal.comso that anti-virus vendors and security researches can analyze it further (2) copy the email content with headers to anti-spam tools like spamcop.net so that the source of the spam campaign can be shut down sooner than later
With awareness and proper training, you can keep your systems safe from evolving threats like ransomware and make sure that no one in your organization clicks and puts your data in a hostage situation.
Learn more about
TELUS Security Solutions for your business
.Authored by:
TELUS Business


